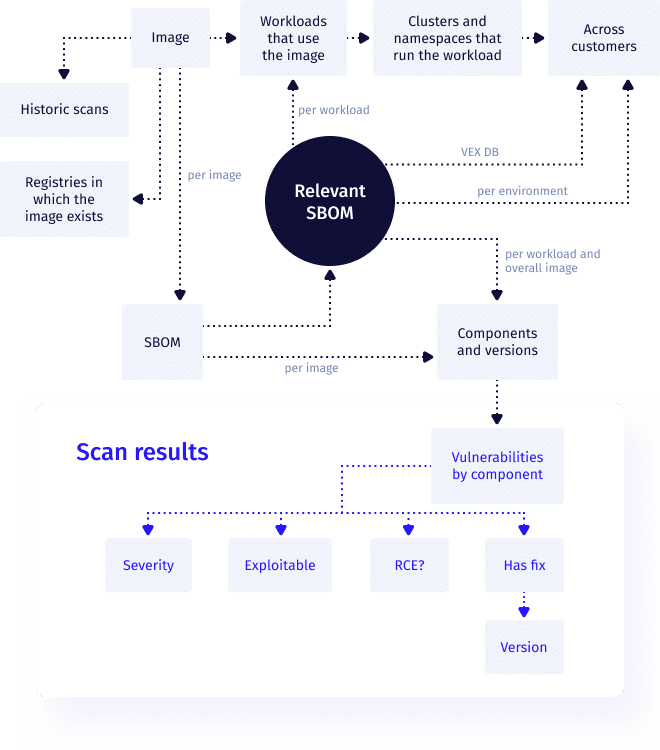
Vulnerabilities In Use
The In Use functionality will enable ARMO users to understand which of the vulnerable packages is currently loaded into the memory
Overview
ARMO's In Use (aka Taster) is based on eBPF. It scans the running environment and maps out artifacts and libraries that are loaded into memory and therefore are in use in the environment.
The Taster is part of ARMO's in-cluster components. It uses eBPF probes to look at the file activity of a running container. When a pod starts on a node, the Taster will watch its containers for a configurable learning period and store an activity log.
During the process of scanning a container, an SBOM is generated. This contains the vulnerability scanner’s understanding of which components are installed in the container. When vulnerabilities are checked the engine is provided with a filtered SBOM, including the packages that relate to files that were accessed during the learning period.
Configure the 'In Use' capability
To configure the configurable learning periods of the feature use the following flags:
| Flag | Default | Description | Configurable |
|---|---|---|---|
| learningPeriod | 2 minutes | The learning period is the amount of time the Taster will observe a running container to determine the relevancy of files. The value represents the minutes | --set nodeAgent.config.learningPeriod=15 |
| maxLearningPeriod | 180 minutes | The max learning period is the amount of time the Taster will observe a running container. The value represents the minutes | --set nodeAgent.config.maxLearningPeriod=200 |
Prioritize workloads with the 'In Use' Vulnerability filter
After installation, the Taster will start listening for every new / restarted container for the time configured in the learning period. Once the learning period is concluded the relevant information will be available in the cluster storage and ARMO Platform. Taster will keep listening for the container until the maxLearningPeriod is reached.
Vulnerabilities - Workloads view
- Navigate to the Vulnerabilities section
- Click on the Vulnerabilities filter
- Mark the 'In Use' checkbox (notice the numbers under the Vulnerabilities column go down)
- The table will show only workloads that contain vulnerabilities which their vulnerable package loaded to the memory. Hence, it is In Use.
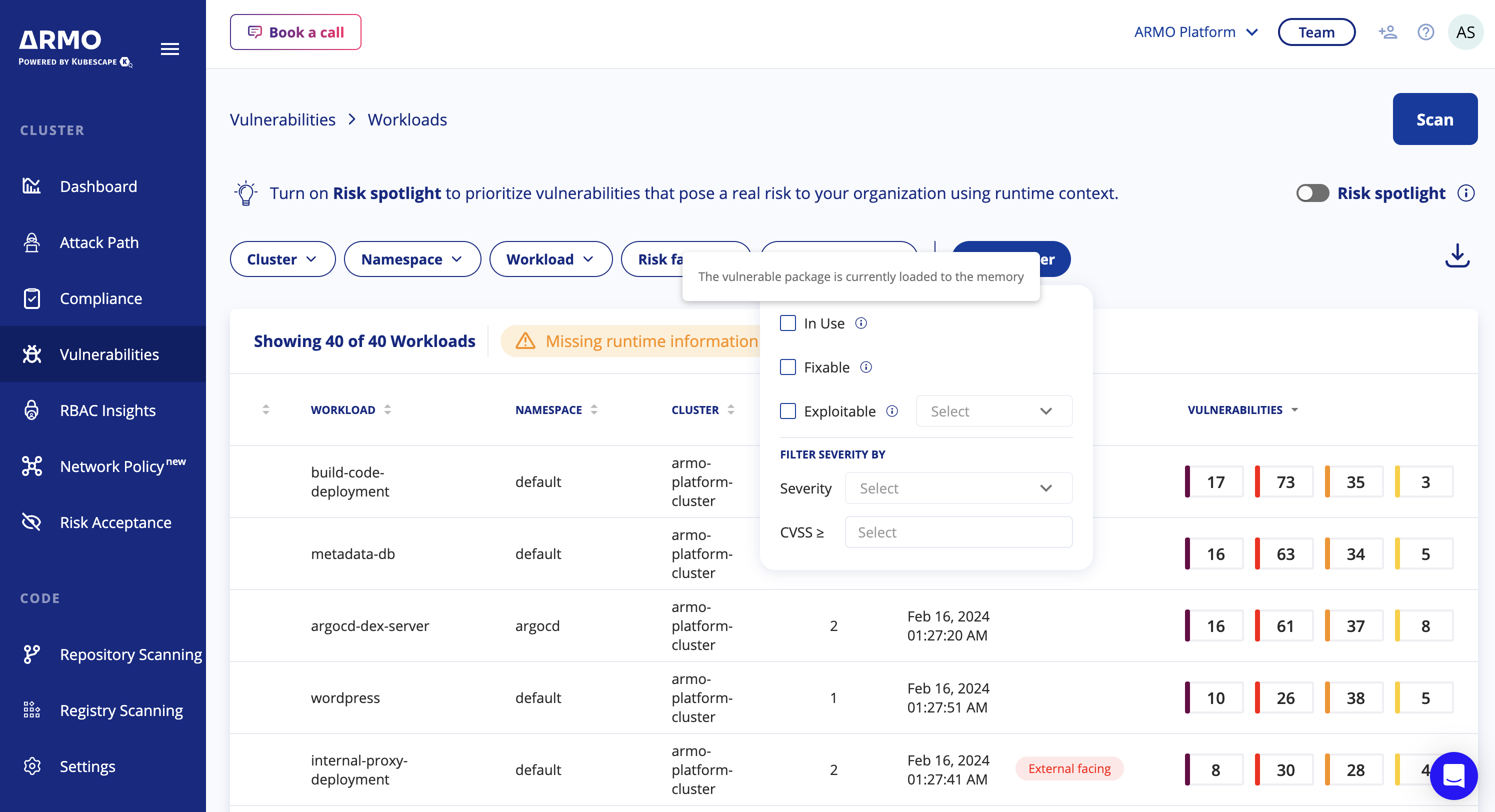
Workload - Missing runtime info
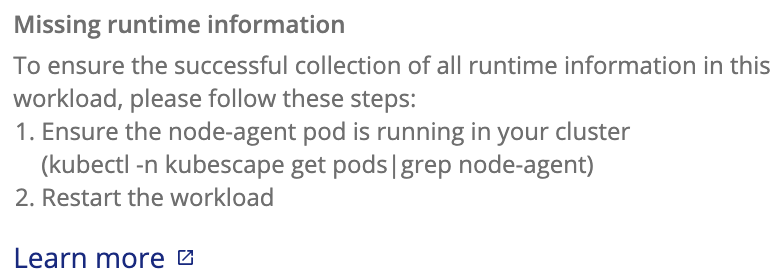
Upon drilling down into a workloads table, some of the workloads might contain a warning sign indicating Missing runtime info with the following explanation:
See here how to troubleshoot Missing runtime info
View relevant information from the cluster storage
View SBOM information
% kubectl get -n kubescape --show-labels SBOMSPDXv2p3
NAME CREATED AT LABELS
0349106521d476e8a833088c33f6db5ac4c898f00d1b6b6f15d9902ff5fdd0f4 2023-04-23T09:07:47Z kubescape.io/image-name=gcr-io-vmwarecloudadvocacy-acmeshop-order
0f232ba18b63363e33f205d0242ef98324fb388434f8598c2fc8e967dca146bc 2023-04-23T09:04:23Z kubescape.io/image-name=gke-gcr-io-cluster-proportional-autoscaler
1198b3b3f1e324799012d0634e96ef99e43831cdb240749f7ceaaab551b09622 2023-04-23T09:15:28Z kubescape.io/image-name=quay-io-kubescape-kubevuln
13964b29d63efcd1490d1a500c4332c642655fe4ca613683fa4dde9a205dd0f7 2023-04-23T09:14:05Z kubescape.io/image-name=ghcr-io-dexidp-dex
1d20492ca374191e5b6ff4b7712b62b41ab75ce226424974356dc266e6e99e83 2023-04-23T09:04:06Z kubescape.io/image-name=gke-gcr-io-metrics-server
20b172e673454b675cade099b95125fb1ce01b53fbf99c5b6260e048174060b1 2023-04-23T09:08:29Z kubescape.io/image-name=gcr-io-google-samples-microservices-demo-frontend
View filtered SBOM information
% kubectl get -n kubescape --show-labels SBOMSPDXv2p3Filtered
NAME CREATED AT LABELS
0207f7055a0a13a655efe073c320de83219ca19e396e37e1bdcc83de976ca99a 2023-04-23T10:05:48Z kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=redis,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=argocd-redis,kubescape.io/workload-namespace=argocd
0d69953f27f65b0546fbd29b12849368cbc5a0cf358b828ee31fbe2865279dea 2023-04-23T10:06:07Z kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=main,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=loadgenerator,kubescape.io/workload-namespace=onlineboutique
28372aa3a8dfdebb9cd2561f85beabbe58fbeb67060c3bde74a061c62923183f 2023-04-23T10:05:49Z kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=argocd-notifications-controller,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=argocd-notifications-controller,kubescape.io/workload-namespace=argocd
30c70b40821cd009b417167b2280cd9d2df4e4eef8dff79f3c7f9a8ee7d75672 2023-04-23T10:05:42Z kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=payment,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=payment,kubescape.io/workload-namespace=acme-fitness
Get CVE list & relevant CVE list
% kubectl get -n kubescape --show-labels VulnerabilityManifests
NAME CREATED AT LABELS
0207f7055a0a13a655efe073c320de83219ca19e396e37e1bdcc83de976ca99a 2023-04-23T10:56:39Z kubescape.io/context=filtered,kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=redis,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=argocd-redis,kubescape.io/workload-namespace=argocd
0349106521d476e8a833088c33f6db5ac4c898f00d1b6b6f15d9902ff5fdd0f4 2023-04-23T09:07:53Z kubescape.io/context=non-filtered
0d69953f27f65b0546fbd29b12849368cbc5a0cf358b828ee31fbe2865279dea 2023-04-23T10:56:42Z kubescape.io/context=filtered,kubescape.io/workload-api-group=apps,kubescape.io/workload-api-version=v1,kubescape.io/workload-container-name=main,kubescape.io/workload-kind=Deployment,kubescape.io/workload-name=loadgenerator,kubescape.io/workload-namespace=onlineboutique
Limitations
Linux kernel
The relevancy functionality is based on eBPF technology which is implemented only on Linux kernels. Therefore the feature will work only on Linux distributions. The Linux kernel version in the node must be >= 5.4.
Updated 2 months ago
